taliesin:/home/russ/VAS/src/preflight # sudo wireshark &*
To see what’s going on on port 88, go to
Then use/reuse Capture->Start, Stop or Restart and see the pretty colors.
* If you get an error like
russ@taliesin:~/VAS/src/preflight> sudo wireshark & [3] 23994 russ@taliesin:~/VAS/src/preflight> (wireshark:23994): Gtk-WARNING **: cannot open display: [3]+ Exit 1 sudo wireshark
Try this instead:
taliesin:/home/russ/VAS/src/preflight # gnomesudo wireshark &
You can't run wireshark unless you are root. On Ubuntu or other systems, you might find the working GUI sudo command to be something like gksudo.
On openSuSE Linux 10.3, I'm finding that the command is
gnomesu -c wireshark &.
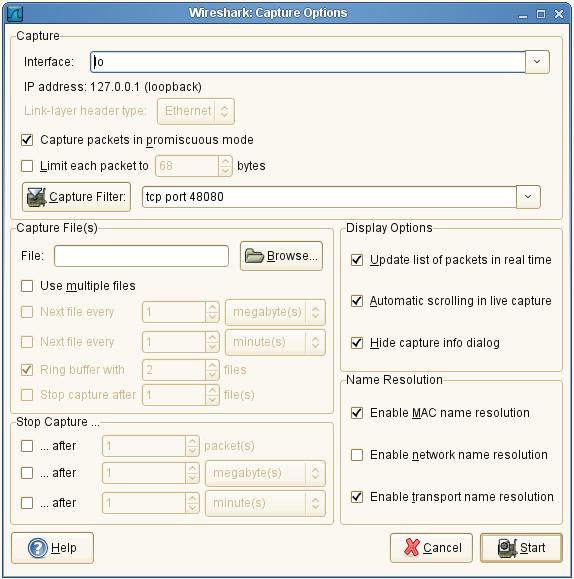
Upon launching wireshark, I pull down the Capture menu, choose Options..., then ensure that the Interface is eth0 (my network card).
I then specify a filter. The filter syntax appears inconsistent between the various places you can set on in wireshark. In one case where I was attempting to sniff HTTP exchanges between two applications I was testing, I set the Interface to lo (meaning local or 127.0.0.1) and then used tcp port 48080.
Then, click on the Start button and the fun begins. (You're on your own now.)

Leaving the Interface: as eth0, I use a capture filter of tcp port 443 to take a look at some HTTP requests I'm exchanging with an Amazon S3 cloud. I get the packets, but they're all donkey spit because the exchange is in HTTPS.
In extreme need, check out www.charlesproxy.com; not sure how to ensure that this proxy gets used, try:
russ@taliesin:~/dev> export http_proxy="http://127.0.0.1:8888 [http://127.0.0.1:8888]"