Basic Authentication Walk-through
Seth Ellsworth
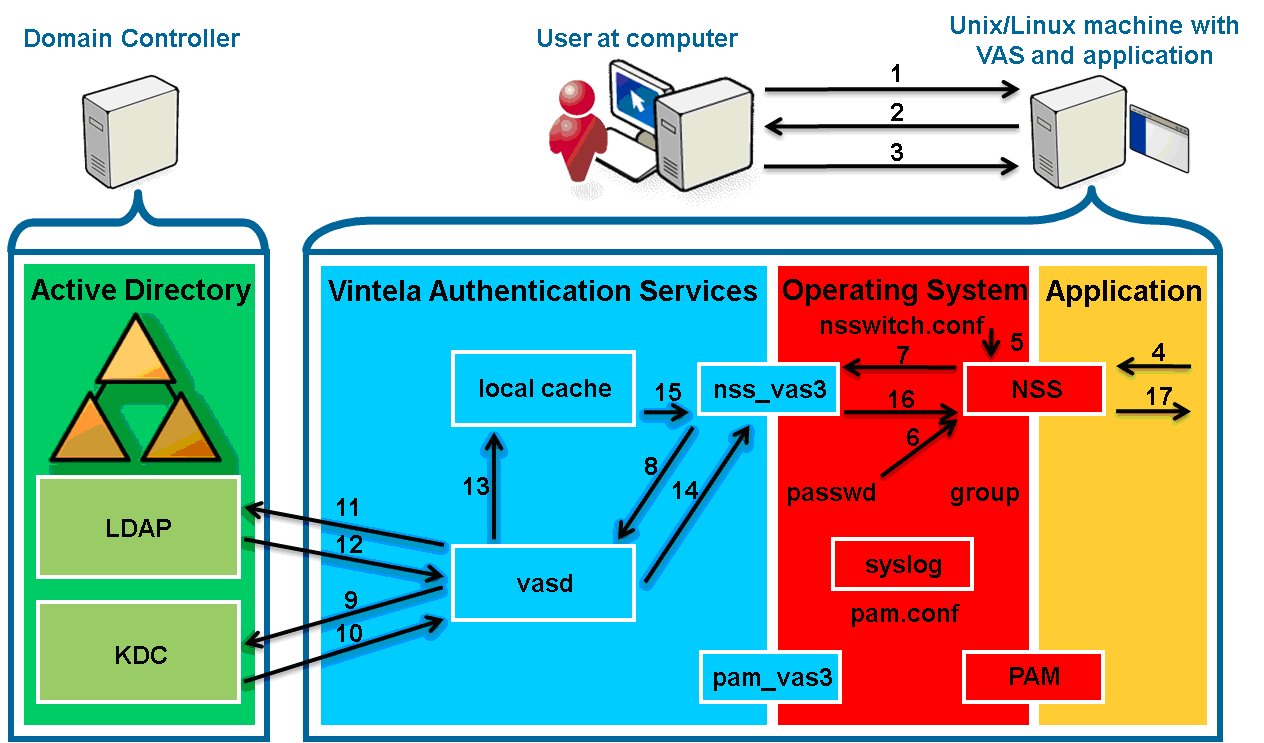
- 1. The user opens a secure connection with the application.
- 2. The application sends a prompt for the username.
- 3. The user’s sends a username to the application.
- 4. The application queries NSS (using getpwnam) about the user.
- 5. NSS reads /etc/nsswitch.conf and processes the
passwd: files vas3 entry.
- 6. NSS queries nss_files which reads /etc/passwd and returns
ENOENT because no matching user entry is found.
- 7. NSS queries nss_vas3.
- 8. nss_vas3 sends an interprocess communication (IPC) to
vasd to update the user.
- 9. vasd uses credentials from the keytab to request a ticket to
talk to the LDAP/ service in Active Directory (AD).
- 10. AD key-distribution center (KDC) returns the requested service ticket.
- 11. vasd queries AD LDAP for the user information.
- 12. The user’s information is returned.
- 13. vasd writes the user information into its local cache
(persistence database).
- 14. vasd responds to nss_vas3 that it has updated the
user.
- 15. nss_vas3 queries the local cache and formats the data into a
passwd-style response.
- 16. nss_vas3 returns the passwd info to NSS. Note: There is no
password hash since vasd does not have access to that unless
using a legacy authentication setup.
- 17. NSS returns the information to the application.
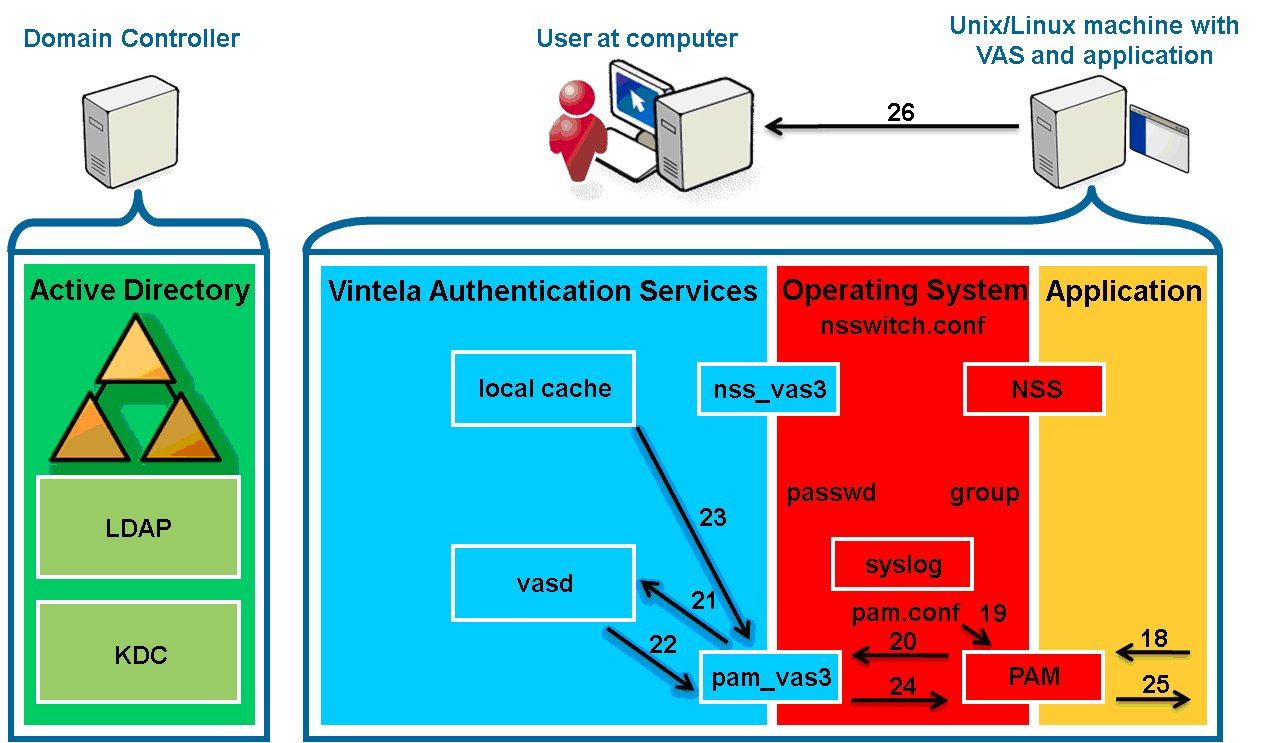
- 18. The application calls PAM through pam_start then
pam_authenticate.
- 19. PAM reads /etc/pam.conf and processes the pam_vas3 entry.
- 20. PAM queries pam_vas3.
- 21. pam_vas3 sends a forced update request for the user to
vasd.
- 22. Since the request is made within 10 seconds of the previous request
for the same user, vasd does not update it again. Returns
that the user is updated.
- 23. pam_vas3 queries the local cache for the user information.
The user is a VAS user so pam_vas3 will continue to attempt
to authenticate the user instead of ignoring and letting the PAM
stack fall past pam_vas3.
- 24. pam_vas3 returns a request for credentials (password) using
PAM conversations including the prompt to use.)
- 25. PAM returns the request to the requesting application.
- 26. The application presents the user with the prompt for a password. (If
the application is PAM conversation-aware, it uses the prompt
pam_vas3 set).
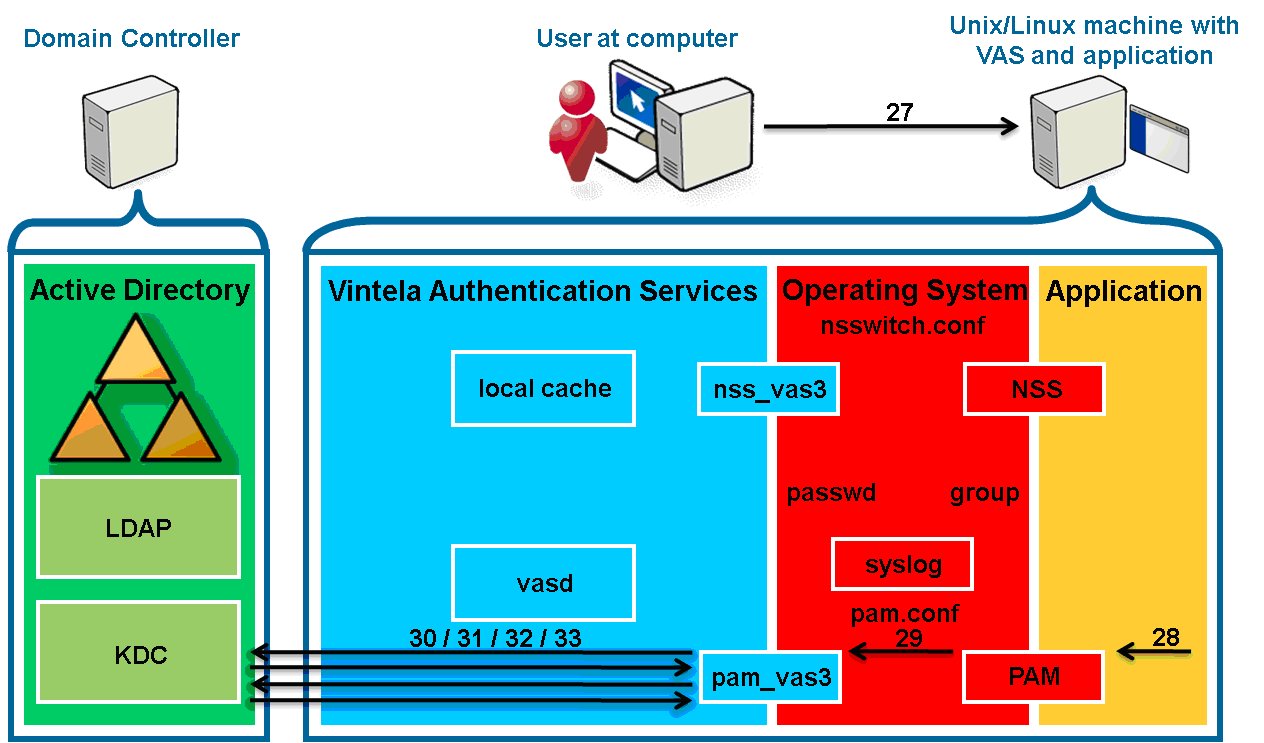
- 27. The user enters a password.
- 28. The application passes the password to PAM.
- 29. The password is passed back to pam_vas3 through the
conversation mechanism.
- 30. pam_vas3 requests a Kerberos ticket-granting ticket (TGT)
for the user via a user key derived from the user’s
samaccountname@realm and the supplied password. Kerberos does
not use passwords: it uses keys derived from them for security. Thus,
no passwords, even encrypted ones, are ever transmitted over the wire.
- 31. AD KDC returns the TGT (AS-REP).
- 32. pam_vas3 decrypts the response using the user key, obtaining
a TGT and session key. The TGT and session key are used to request a
service ticket (TGS-REQ) from the AD KDC for the user to authenticate
against the “host/” (local machine) service.
- 33. The AD KDC returns the service ticket (TGS-REP), which is decrypted
using both the session key (user portion) and the “host/”
key (service portion) that is stored in the host.keytab file.
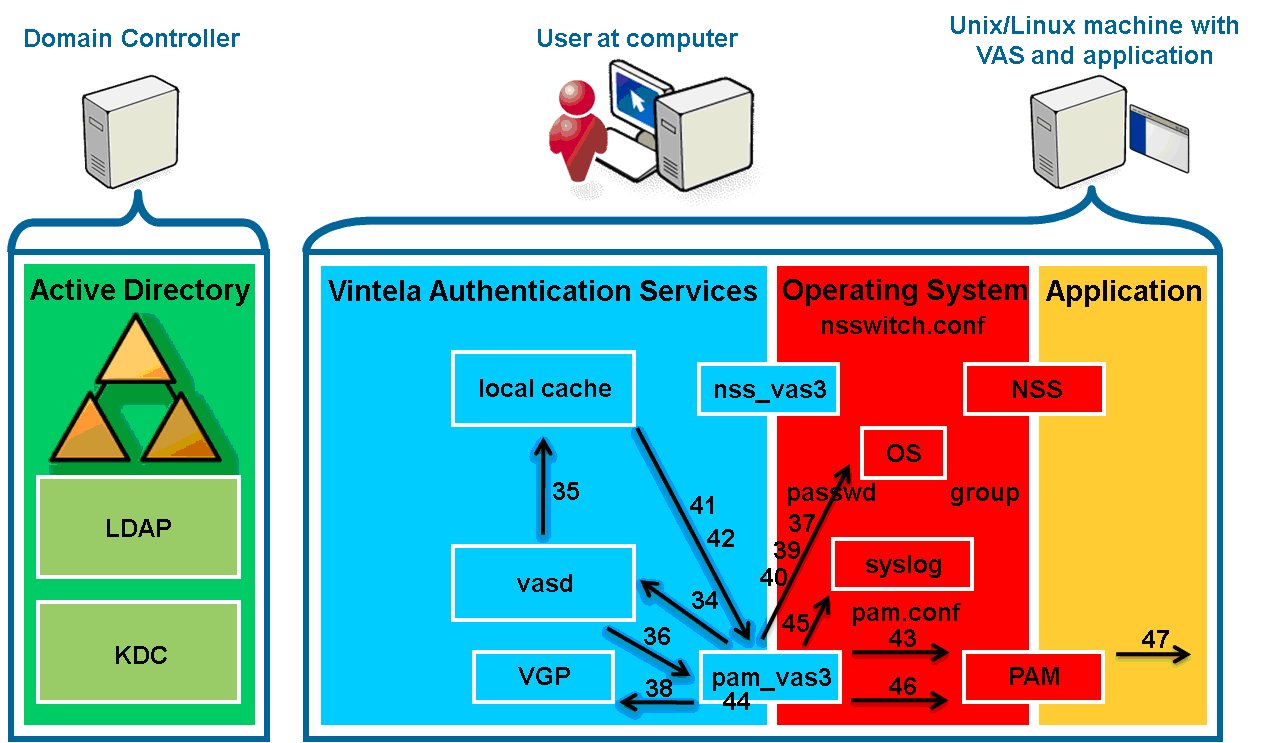
- 34. pam_vas3 processes the payload of the service portion of the
service ticket, which is the privileged access certificate (PAC), a
list of SIDs of groups of which the user is a member, and sends these
through a secure IPC to vasd.
- 35. vasd modifies the local cache to set the current group memberships.
- 36. vasd returns success to pam_vas3.
- 37. pam_vas3 creates the user’s home directory if needed.
- 38. pam_vas3 calls VGP to apply any user policies.
- 39. pam_vas3 stores the user’s TGT and “host/”
service ticket in the local cache for the user to use again if
desired.
- 40. pam_vas3 sets the environment variable VAS_LOGONSERVER to
the server used for auth (this is not guaranteed to be in effect in
the user’s final shell), and fills the
~/.vas_logon_server file with the server name.
- 41. pam_vas3 reads the user account information from the local
cache. It verifies the user is within any configured login hours and
has a valid shell (not /bin/false in AD).
- 42. pam_vas3 queries the local cache for the user’s group
membership information and confirms that the user has access based on
any configured access control.
- 43. pam_vas3 sets a PAM stack variable to note that it has
already processed the above. (This is a per-authentication local
variable).
- 44. pam_vas3 performs UID and GID conflict checking.
- 45. pam_vas3 writes a syslog entry that the authentication
succeeded.
- 46. pam_vas3 pam_authenticate returns
PAM_SUCCESS.
- 47. Because the pam_vas3 entry is configured with
sufficient, PAM_SUCCESS is returned to the querying
application, ignoring the rest of the PAM stack.
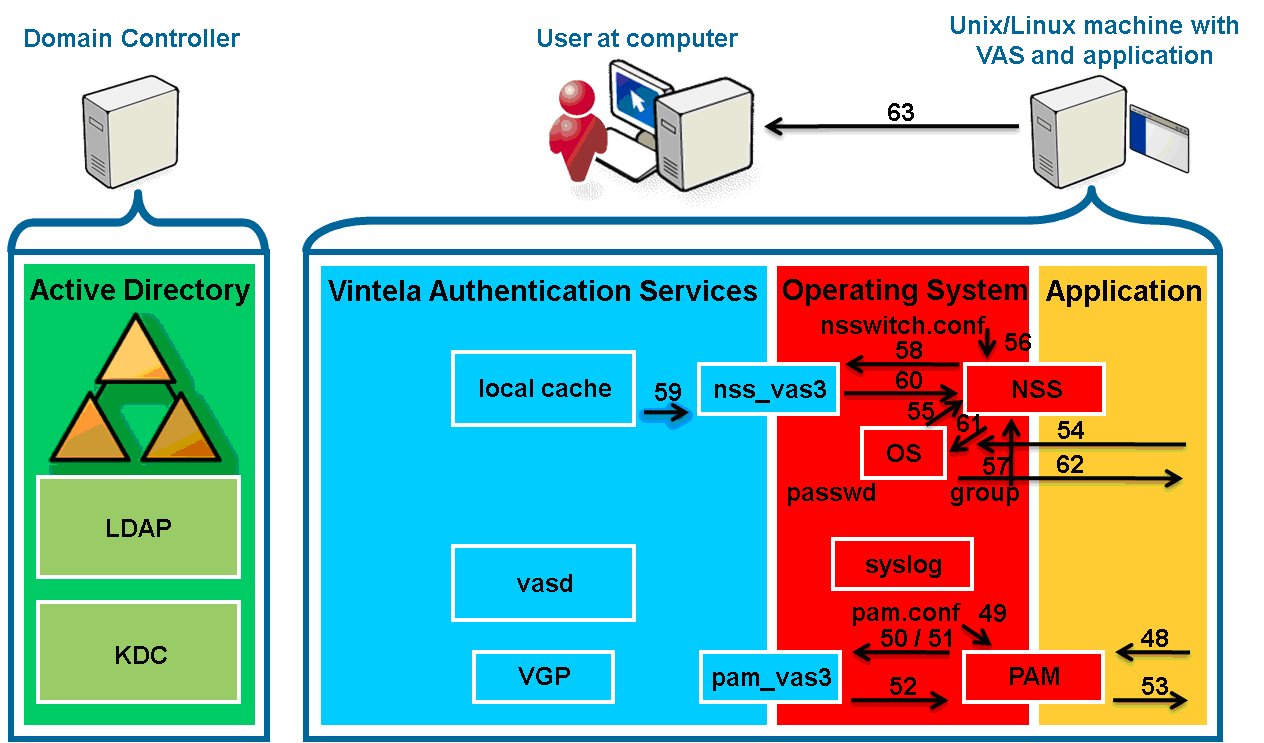
- 48. The application calls PAM, through pam_acct_mgmt and
pam_open_session.
- 49. PAM reads /etc/pam.conf and processes the pam_vas3
entry.
- 50. PAM queries pam_vas3 for pam_acct_mgmt and
pam_open_session.
- 51. pam_vas3 reads the variable set in step 43.
- 52. pam_vas3 returns PAM_SUCCESS to PAM for each call.
These functions are used mainly during non-password authentication
(GSSAPI, ssh keys, etc.) and password changes.
- 53. PAM returns PAM_SUCCESS to the application for both calls.
- 54. The application starts the user’s shell which then sets up the
environment.
- 55. The OS/shell calls NSS getgroups for the user’s group
memberships.
- 56. NSS reads /etc/nsswitch.conf and processes the
group: files vas3 entry.
- 57. NSS queries nss_files which reads /etc/group and adds
no groups if no local groups contain the user.
- 58. NSS queries nss_vas3.
- 59. nss_vas3 queries the local cache to compute the user’s
group memberships.
- 60. nss_vas3 returns the memberships to NSS.
- 61. The shell uses the groups to set the process space group memberships.
- 62. The OS presents the shell to the application.
- 63. The application presents the shell to the user who is now logged in.





