$ keytool -genkeypair -keyalg RSA -alias mdmi -storetype PKCS12 -keystore mdmi-keystore.pkcs12 -validity 365 -keysize 2048 $ keytool -export -alias mdmi -file mdmi-keystore.crt -storetype PKCS12 -keystore mdmi-keystore.pkcs12 -storepass changeit $ keytool -import -noprompt -trustcacerts -alias mdmi -file mdmi-keystore.crt -storetype PKCS12 -keystore mdmi-truststore.pkcs12 -storepass changeit
~/dev/nifi/nifi-1.15.0/conf $ keytool -list -v -keystore mdmi-keystore.pkcs12 Enter keystore password: changeit Keystore type: PKCS12 Keystore provider: SUN Your keystore contains 1 entry Alias name: mdmi Creation date: Jul 21, 2022 Entry type: PrivateKeyEntry Certificate chain length: 1 Certificate[1]: Owner: CN=windofkeltia.com, OU=Unknown, O=Wind of Keltia, L=Provo, ST=UT, C=US Issuer: CN=windofkeltia.com, OU=Unknown, O=Wind of Keltia, L=Provo, ST=UT, C=US Serial number: 3991a09e Valid from: Thu Jul 21 13:17:06 MDT 2022 until: Fri Jul 21 13:17:06 MDT 2023 Certificate fingerprints: SHA1: 28:1A:C0:9D:CE:E7:B3:51:EA:62:0F:75:2D:69:54:DC:41:B8:B2:DF SHA256: 0C:B8:90:24:E0:22:AF:64:AB:9F:FB:CF:4F:9E:45:B9:07:2D:FA:19:91:D3:46:18:53:25:00:96:CD:F6:97:B6 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 14 7C B7 AE 6D AB 8D DE 19 9C 05 A8 1A 37 6B 66 ....m........7kf 0010: E8 49 41 A1 .IA. ] ] ******************************************* ******************************************* ~/dev/nifi/nifi-1.15.0/conf $ keytool -list -v -keystore mdmi-truststore.pkcs12 Enter keystore password: changeit Keystore type: PKCS12 Keystore provider: SUN Your keystore contains 1 entry Alias name: mdmi Creation date: Jul 21, 2022 Entry type: trustedCertEntry Owner: CN=windofkeltia.com, OU=Unknown, O=Wind of Keltia, L=Provo, ST=UT, C=US Issuer: CN=windofkeltia.com, OU=Unknown, O=Wind of Keltia, L=Provo, ST=UT, C=US Serial number: 3991a09e Valid from: Thu Jul 21 13:17:06 MDT 2022 until: Fri Jul 21 13:17:06 MDT 2023 Certificate fingerprints: SHA1: 28:1A:C0:9D:CE:E7:B3:51:EA:62:0F:75:2D:69:54:DC:41:B8:B2:DF SHA256: 0C:B8:90:24:E0:22:AF:64:AB:9F:FB:CF:4F:9E:45:B9:07:2D:FA:19:91:D3:46:18:53:25:00:96:CD:F6:97:B6 Signature algorithm name: SHA256withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 3 Extensions: #1: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: 14 7C B7 AE 6D AB 8D DE 19 9C 05 A8 1A 37 6B 66 ....m........7kf 0010: E8 49 41 A1 .IA. ] ] ******************************************* *******************************************
First, I used conf/mdmi-keystore.pkcs12, etc., but in
Configure Apache NiFi StandardRestrictedSSLContextService Controller Service,
I saw someone assert that full paths are needed, so I began doing that.
Keystore Filename: /home/russ/dev/nifi/nifi-1.15.0/conf/mdmi-keystore.pkcs12
Keystore Password: changeit
Key Password: changeit
Keystore Type: PKCS12
Truststore Filename: /home/russ/dev/nifi/nifi-1.15.0/conf/mdmi-truststore.pkcs12
Truststore Password: changeit
Truststore Type: PKCS12
TLS Protocol: TLS
Keystore Properties is invalid because invalid keystore password or type specified for file conf/mdmi-keystore.pkcs12 Truststore Properties is invalid because invalid truststore password or type specified for file conf/mdmi-truststore.pkcs12
I tried StandardSSLContextService in lieu of StandardRestrictedSSLContextService.
Validation still failed.
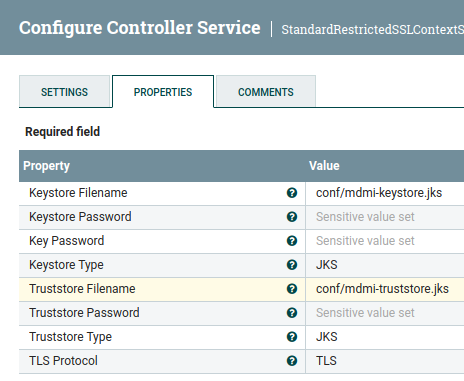
I show JKS here as store type, but that was the first time around. Later I
standardized on using PKCS12.
You see that just above here in oppostion to the
older illustration posted below.
First, my question as I posed it in the Apache NiFi User's forum...
I have hesitated between providing some huge tl;dr exposé and something shorter. I'll do shorter here.
Keystore Properties is invalid because invalid keystore password or type
specified for file __________.
Truststore Properties is invalid because invalid truststore password or type
specified for file __________.
It would be nice to see a step-by-step illustration of creating the key, key store and trust store artifacts required by SSL context service and perhaps the full configuration of the SSL context service.
Other notes:
Huge thanks for any help or comments.
And now the answers...
Is Tomcat using a CA-signed certificate? If so, you should leave the InvokeHTTP property SSLContextService blank. This will cause InvokeHTTP to use the default JVM truststore, which trusts CA-signed certificates. If you can access your Tomcat from a web browser without certificate warnings, the certificate is likely CA-signed.
If Tomcat is using a self-signed certificate, you'll need to assemble a truststore using the self-signed certificate. Download the certificate, and use the instructions above to assemble the truststore.
One more bit of information. InvokeHTTP uses an open source library that expects the server hostname to match a distinguished name defined in the certificate.
Hope this helps...
(Paul Grey)
For PKI, you always need a truststore and a keystore. You can have them reside in the same place (not recommended) and/or you could just trust everything (again, not recommended), and/or your app (eg: Tomcat) could be default configured so that is does the risky "not recommended" things mentioned above. But that doesn't mean that "no trust store is needed or involved".
There are some good tutorials out there for using keytool and openssl for
setting up PKI for client/server 2-way authentication.
(Patrick Timmins)